| Overview of Deploying Active Directory in Branch Office Environments |
To meet the special requirements of the branch office scenario, deploying the Active Directory® directory service in a branch office environment requires additional configuration beyond that of a normal Active Directory deployment. The Planning section of this guide describes how to examine your needs and use the recommendations provided to create a deployment plan for your branch office environment. This section of the document describes the process of implementing the deployment plan.
This section uses the same sample company as the Planning section. The procedures outlined here are based on deploying the sample company Contoso Pharmaceuticals based on the model established in the Planning section.
This guide is intended for network managers, system integrators, and consultants who are involved in Active Directory branch office implementations, either in their own organizations or for client companies. By implementing the procedures in this document, you should be able to deploy and maintain Active Directory in a large branch office environment. For the purposes of this guide, a large branch office environment is considered to be a deployment in which at least one data center is attached to 100 or more branch offices.
This section of the guide breaks down the deployment process into seven phases. Each chapter covers one phase, beginning with the creation of your forest, and provides the steps necessary to create your sites, deploy the staging servers, and deploy your branch office domain controllers.
As with any large technology project, having the right resources for planning and deployment is essential. The resources that you will require for an Active Directory branch office deployment fall into three categories: hardware, software, and personnel. Your specific resource requirements will depend on a number of factors, including project scope, solution features, implementation schedule, and budget. In addition, the skill level and makeup of your existing Active Directory services team will affect your needs for team training and external resources.
The specific hardware requirements for Active Directory depend on the expected service level and load that are defined in the Vision Scope and other planning documents. For example, the number of branches that will be serviced by each bridgehead server and the expected replication load during each replication connection will impact the processor and memory requirements for the bridgehead servers. In addition, the load generated by client and server DNS queries and the number and frequency of directory look-ups from directory-enabled applications will impact hardware requirements in terms of configuration and quantity. Additional help for capacity planning can be found in the Microsoft® Windows® Server 2003 Deployment Kit on the Web at http://go.microsoft.com/fwlink/?linkID=8022.
The following table lists the software required for deploying Active Directory in a branch office environment.
Table .1 Software Required to Deploy Active Directory in a Branch Office Environment
| Item | Description | Details |
| Microsoft® Windows Server™ 2003, Standard Edition, Windows Server Enterprise Edition, or Windows Server Data Center Edition operating system | The version of Windows Server 2003 you require will depend on the size of your organization or the installed base in your datacenter. All editions of the Windows 2003 Server family are capable of providing Active Directory services in your branch office environment. | Note that Enterprise Edition is required for the ADS server in the staging site (discussed later in this document). For all other installations, the version you choose for the domain controllers can be based on your requirements. |
| Microsoft Windows Server 2003 Resource Kit Tools | This collection of tools (included with the Windows Server 2003 Deployment Kit) can help you deploy, configure, maintain, and troubleshoot Windows Server 2003: | Download the Windows Server 2003 Resource Kit Tools from the Microsoft Download Center on the Web at http://go.microsoft.com/fwlink/?LinkID=20334 |
| Windows Server 2003 Deployment Kit | This kit delivers additional information and tools for deploying the Windows Server 2003 operating system. | Download the Windows® Server 2003 Deployment Kit on the Web at http://go.microsoft.com/fwlink/?linkID=8022. |
| Automated Deployment Service (ADS) | ADS is used for the automated partitioning and setup of branch office domain controller operating systems. | The ADS server, located in the staging site, requires Windows Server 2003, Enterprise Edition. |
| Active Directory branch office installation files | These files are downloaded with this guide and are stored in a self extracting executable named ADBranch03.exe. | When the files are extracted they are stored in the c:\ADBrancho3 folder. |
The following table lists the software that is recommended for monitoring.
Table .2 Recommended Software to Monitor the Branch Office Deployment
| Item | Description | Details |
| Microsoft Operations Manager (MOM) | Microsoft Operations Manager is used for monitoring in the Hub-Site site. | |
| Branch Office Monitor | Branch Office Monitor is used to run some of the monitoring tools and ensures the monitoring in the Branch Offices. | |
| Ultrasound and Microsoft Windows File Replication Service Management Pack | Ultrasound is a robust tool for monitoring and troubleshooting FRS. The Microsoft Windows File Replication Service Management Pack is a bridge from Ultrasound to the MOM console | Ultrasound can be found at the Microsoft Download Center at http://go.microsoft.com/fwlink/?LinkId=26675. The Microsoft Windows File Replication Service Management Pack can be found at the Microsoft Download Center at http://go.microsoft.com/fwlink/?LinkId=26677 |
| Active Directory Management Pack (ADMP) | ADMP is the management pack that allows Active Directory monitoring in a MOM environment. | The Active Directory Management Pack (ADMP) can be downloaded from the Microsoft Download Center at http://go.microsoft.com/fwlink/?LinkId=26678 |
| Microsoft SQL Server™ 2000 | Microsoft SQL Server is needed to host the MOM database | |
| Microsoft SQL Server 2000 Service Pack 3 | Service Pack 3 is required to install Microsoft SQL Server 2000 on a Windows Server 2003 domain controller | Service packs for SQL Server can be downloaded from the Microsoft SQL Server web site at http://go.microsoft.com/fwlink/?LinkId=26680 |
Base Operating System Installation
The procedures in this guide assume that you are starting with a server that already has the base operating system installed. For a branch office deployment, the operating system can be Windows Server 2003 Standard Edition, Windows Server 2003 Enterprise Edition, or Windows Server 2003 Data Center Edition. This guide assumes that you are using Windows Server 2003 Standard Edition with one exception: The server running Automated Deployment Services (ADS) must be running Windows Server 2003 Enterprise Edition.
| Important This guide assumes that all available Service Packs and any outstanding critical updates have been installed. Please contact Microsoft Product Support Services to acquire the updates associated with the Knowledge Base articles listed in this section. |
The recommendations in this guide require the installation of the updates in the following articles, which can be found in the Microsoft Knowledge Base. To find these articles, see the Microsoft Knowledge Base on the Web at http://go.microsoft.com/fwlink/?LinkID=4441:
· 823230 - “Issues That Are Resolved in the Pre-Service Pack 1 Release of Ntfrs.exe”
· 824333 - “DNS records used for AD replication may not register on desired DNS Server”
· 824334 - “Branch Office Mode May Not Result in Balanced Connections”
· 824335 - “Hub site domain controllers may not perform inbound replication according to schedule“
· 830092 - “W32Time frequently logs Event ID 50 and poor time synchronization occurs on Windows Server 2003”
In addition to the operating system, this guide assumes that the Windows Server 2003 Support Tools have been installed from the product CD, as well as the Windows Server 2003 Resource Kit Tools, which are available from the Microsoft Download Center on the Web at http://go.microsoft.com/fwlink/?LinkID=20334.
Monitoring Solutions
Three monitoring solutions are discussed in this guide. Based on the decisions you make for your monitoring options you will need access to the installation files for one or more of these solutions. The installation files for these solutions can be found at the following locations:
Branch Office Monitor - Included in the self extracting exe file accompanying this guide.
Ultrasound - Go to www.microsoft.com and search on “FRS Monitoring”
Active Directory Management Pack - Go to www.microsoft.com and search for “Microsoft Operations Manager Downloads”. Note: Microsoft Operations Manager is required in order for you use the Active Directory Management Pack.
Notes Regarding Specific Versions of Tools
Throughout this guide you will find procedures requiring the use of the following tools:
· ADLB.exe
· Dcdiag.exe
· Repadmin.exe
Although versions of these tools are available through the Windows Server 2003 Resource Kit Tools (ADLB) and the Windows Server 2003 Support Tools (Repadmin and Dcdiag), updated versions have been included in the self-extracting executable file that accompanies this guide.
All procedures in this guide assume you are using the version that is included with the guide.
| Important After installation of the scripts that accompany this guide, which occurs in Chapter 2 of this guide, the updated versions of ADLB.exe, Dcdiag.exe, and Repadmin.exe are located in the C:\ADBranch03\Bin\Tools\x86 folder. A procedure is included in this guide to copy ADLB.exe to the appropriate folder. However, to ensure that you are using the proper version of Repadmin and Dcdiag, you must first install Windows Support Tools and then copy the updated versions of Repadmin.exe and Dcdiag.exe from C:\ADBranch03\Bin\Tools\x86 to C:\Program Files\Support Tools. |
Active Directory affects your entire organization, so it should not be surprising that the personnel involved in its deployment will cross all boundaries in a company. It is necessary to establish typical roles within an Active Directory environment and within a project team.
Typical roles within the Active Directory environment are:
· Service Administrators
· Data Administrators
· Forest Owner
· Active Directory DNS Owner
· Site Topology Owner
· OU Owner
The roles and responsibilities within a project team are:
· Architects
· Project Manager
The preceding is only a short overview of the personnel who should be involved in deploying Active Directory in a branch office environment. For a detailed description of how to identify project personnel, see “Identifying the Deployment Project Participants” in Chapter 2, “Designing the Active Directory Logical Structure” in the Windows Server 2003 Deployment Kit.
This guide walks you through the process of building the branch office architecture shown in Figure 1.
Figure 1 Sample Branch Office Environment
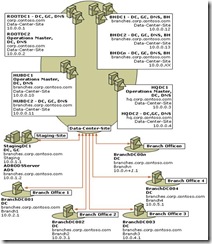
This architecture is based on the sample used in the Planning portion of this guide and is designed using the recommendations outlined in the Planning section. The features in this model include:
· The root domain, corp.contoso.com, has two domain controllers in the hub site. Both domain controllers are DNS servers. The first domain controller is also a global catalog server. The second domain controller holds all operations master roles.
· The HQ office domain, hq.corp.contoso.com, has two domain controllers in the hub site. Both domain controllers are DNS servers. The first domain controller holds all domainwide operations master roles. The second domain controller is a global catalog server.
· The branch office domain, branches.corp.contoso.com, starts with seven domain controllers. All domain controllers are DNS server. The first two domain controllers are not used for intersite replication with the branch sites. The other five domain controllers are used as bridgehead servers. Each bridgehead server is a global catalog server.
· The staging site has a domain controller that is the replication source for the staging process. It also contains the ADS server that is used for the process to build new branch office domain controllers. The staging domain controller is a global catalog server.
· The branch office sites.
The example architecture includes five bridgehead servers. Based on the decisions you made in the Planning Guide, you will need to create the number of bridgehead servers that you determined are necessary for your environment.
This guide will walk you through the configuration of this scenario by giving you instructions for every phase of the deployment. By repeating the domain controller staging process in “Chapter 7 – Installing the Branch Office Domain Controller in the Staging Site,” you can scale out the number of branch offices to meet the requirements of your organization.
The chapters in this guide use the domain names and Internet Protocol (IP) addresses shown in the previous diagram whenever an example is appropriate. Therefore, you will want to have a copy of this diagram available as you go through the chapters and substitute the information in the diagram with your domain name and IP addresses.
During the deployment process some of the steps, such as building the forest root domains and setting up the domain controllers in the hub site, are performed manually by members of the deployment team. Other steps, such as building the branch office domain controllers, use scripts and are almost fully automated.
By following the instructions described in this guide you will perform the following procedures:
· Build the forest root domain
Start by building the first domain controller to establish the forest root domain. Install the DNS Server service and create the DNS environment needed to support the new forest. Add a second domain controller and make it a DNS server also. After the domain controllers have been built and you have verified that Active Directory and DNS are functioning properly, create the hub site that will be used to represent all of the domain controllers located in the data center. Then move the new domain controllers into the new site.
· Build the headquarters domain
Start by building the first domain controller to establish the headquarters domain. This domain is used to represent the head office or the portion of the organization that is located in the hub site of your model. Install the DNS Server service and integrate this domain into the existing DNS environment that has been created for the forest. Add a second domain controller and install DNS on this server also. After the domain controllers have been built, verify that Active Directory and DNS are functioning properly and verify that they are in the hub site.
· Build the branch office domain
Build the first domain controller to establish the domain that will be used by your branch offices. This domain will be represented in the hub site and the branch office sites. It will contain all the branch office domain controllers and the bridgehead servers used to replicate with the branch offices. Install the DNS Server service and integrate the new domain into the existing DNS environment that has been created for the forest. Add a second domain controller and install DNS on this server also. After the domain controllers have been built, verify that Active Directory and DNS are functioning properly. After the new domain is installed and functioning properly, build the domain controllers that will be designated as the bridgehead servers. Build each bridgehead server and verify that it is functioning properly before proceeding with the next server. After all of the bridgehead servers are built, create a Group Policy object to suppress service (SRV) locator record registration and apply it to all the domain controllers in the branch office domain. Then set permissions on the Group Policy object to prevent the policy from being applied to the domain controllers in the hub site.
· Build the staging site
Create the staging site and then build a domain controller that will be used for staging the branch office domain controllers. After you have tested and verified that the new domain controller is working properly, prepare the server for its role as the staging server. Configure it as a DHCP server and use it to allocate IP addresses to the new branch office domain controllers that are built in the staging site. Use the staging server to create the media backup set that will be used during the Install From Media process during the branch office domain controller build process.
· Prepare Automated Deployment Services
Add another server to the staging site. Install a database engine and Automated Deployment Services (ADS). Install the tools and scripts that accompany this guide. Add another server to the staging site. Configure it to represent a typical server used to build a domain controller that will be placed in a branch office location. This server will be used as a model to create the image used by ADS to build the branch office domain controllers. You must customize some of the DNS settings on the server so that when a new domain controller is built from the image, it is preconfigured to fit into the branch office environment. Also, if there are any additional files you want distributed on all the branch office domain controllers, make sure you copy them onto the server at this time. If you are planning on implementing a monitoring solution that needs to have components distributed to the branch office locations, such as the Branch Office Monitor, install the necessary files. Once the new server is properly configured and you have installed your additional files, run SYSPREP and then use ADS to create an image of the server. Create an ADS job template and you are ready to begin deploying branch office domain controllers.
· Build the Branch Office Domain Controllers
Most of the process required to build the branch office domain controllers is automated and managed by either ADS or scripts that are included with this guide. Once the job has been created on the ADS server, the process is initiated by using Preboot Execution Environment (PXE) technology to start a new server that you want to turn into a branch office domain controller. When the new server is started, ADS uses PXE to detect the new computer and if the computer is listed in a defined job, ADS begins the build process. ADS uses the server image that was created earlier and builds a new server. Once the build process is complete, the new server is rebooted and scripts automatically start the Active Directory installation process. Using the media backup set, IFM is used during the directory installation process. If any problems occur during this process, information is written to log files that can be used to troubleshoot the problem. The process will continue to automatically restart until no problems are encountered and the process has completed successfully. Details about the scripts that are installed and their individual functionality can be found in commented text inside each of the script files. An overview of how the scripts work together can be found in the Readme.txt file located in the folder C:\ADBranch03\adbodg that gets created when you extract the files from the ADBranch03.exe file accompanying this guide.
· Ship the branch office domain controller
When the build process is complete the scripts will automatically reconfigure the networking settings on the new domain controller so that it is ready to be installed in its branch office location. At that point new domain controller should be shut down and immediately boxed and shipped to its new location. It is best to minimize the amount of time the new domain controller is disconnected from the network during the shipping phase of the deployment. If it is disconnected for too long, it will not replicate with other domain controllers when it is turned back on.
 Read the entire book here for Free. Link
Read the entire book here for Free. Link
 Note
Note 

